“It is not enough to be joint, when conducting future operations. We must find the most effective methods for integrating and improving interoperability with allied and coalition partners. Although our Armed Forces will maintain decisive unilateral strength, we expect to work in concert with allied and coalition forces in nearly all of our future operations, and increasingly, our procedures, programs, and planning must recognize this reality.”
- Gen John M. Shalikashvili, Chairman of the U.S. Joint Chiefs of Staff, Joint Vision 2010
In 2010, the Joint Vision program 1 was developed as a concept for how the United States (US) Armed Forces will channel the ‘vitality’ and ‘innovation’ of its people and leverage technological opportunities to achieve new levels of effectiveness in joint warfighting. Its mission was to focus on achieving dominance across the range of military operations through the application of new operational concepts and to forge a common direction for services in developing unique capabilities within a joint framework of doctrine and programs.
Part of the vision for this program was geared towards building ‘Multinational Operations’. As stated by General John M. Shalikashvili - It isn’t enough just to be joint, when conducting future operations. The US military had to find the most effective methods for integrating and improving interoperability with allied and coalition partners. As stated earlier, the US military and Armed Forces expects to work with allied and coalition forces in nearly all future operations, and this has become reality whereby measures have been proactively introduced in the form of protocols, procedures, programs, and planning.
The Joint Vision program evangelizes that as the world continues to embark through an era of accelerated technological change and advancement. Successful adaptation of new and improved technologies may provide greater increases in specific capabilities. On the other hand, failure to understand and adapt could lead to increased risk such that the armed forces will be incapable of effective counter-operations against adversary forces with more highly sophisticated technology.
At its highest level, the alignment of strategic objectives, worldviews, and doctrines and the willingness of partner nations and allies to work cooperatively to adopt and achieve them can make a coalition whole greater than the sum of its parts. As such, while the US and other coalition partners retain the capability to act unilaterally for their own interests - building, maintaining, and improving allied and coalition partnerships is now vital for effective mission operations in areas around the globe where conflicts escalate and potentially threaten national security across all coalition members.
The quote by General John M. Shalikashvili above perfectly sets the stage for the remainder of this article. The goal of this article is not only illustrating the importance of military organization and cooperation across allied and partner coalitions. We also examine the structure and elements that make up a coalition and identify the common social and technological challenges that impede coalitions. We also address some of the solutions, including how MindLink is positioned to support coalitions with securing coalition communication and collaboration.
The Foundation of Coalitions
“The purpose and focus of cooperation and interoperability within the coalition battlespace is to satisfy the strategic objectives within the given constraints and with the maximum possible efficiency and economy of force”. 2
Before discussing the challenges involved in the creating coalitions and partnership, we must first discuss the purpose of data sharing and how data sharing is facilitated before we can draft and define the requirements of potential solutions.
“Unequal” Technological Partnerships
Not all coalition partners will be as technologically advanced as the next. This maybe the main impediments to coalition data sharing, however it presents one of the greatest opportunities for increased interoperability. For example, there may be technological disparity between nations such as the United States, United Kingdom and its coalition partners. Coalition nations make every attempt to bridge this gap to enable the most optimal and efficient coalition data sharing. This can take the form of both common defense and military technologies and the integration of secure communications and collaboration technologies such to connect the technologies and forces across the coalitions, in real-time.
Data and Intelligence Assets
Data is a strategic asset across all industries. Behind all military operations is intelligence data. Defense data and intelligence is a high-interest commodity and is leveraged in a way that brings both immediate and long-term military advantage against the adversary. Data can be anything from orders, reports, photography, videography, supply-chain, friendly and enemy positions – any and every component that makes up a coalition backed military operation.
Command and control operations are vested in collecting and disseminating data across a diverse and varied command structure and across multiple coalition partners. The faster, more reliably, and secure this data sharing can be accomplished, the more cohesive and transparent the common operating picture becomes. Increased compatibility and shared usage, including common protocols, platforms, and data types, can also help to overcome language barriers among partner nations 3.
The image below describes the US DoD’s data strategy and how this coalition of agencies and departments envisage data. The US DoD’s mandate on data is geared around a Vision, Principles, Capabilities and Goals.
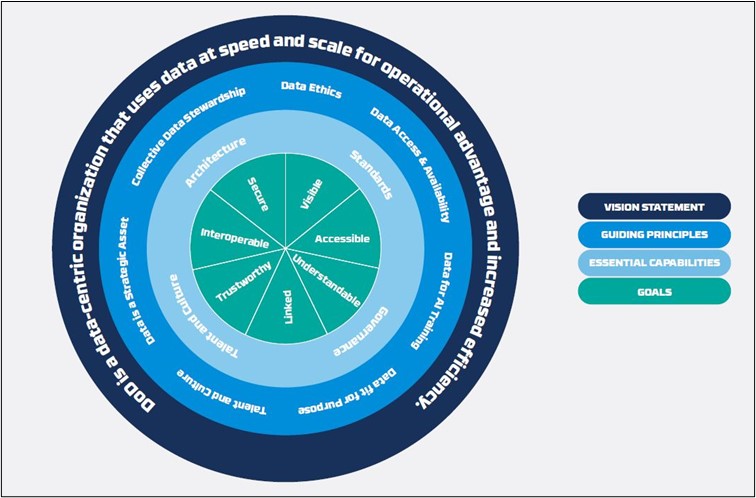 Figure 1 – US DoD Data Mandate and Strategy 4
Figure 1 – US DoD Data Mandate and Strategy 4
Operations – Driving the Coalition War Theater
One of the core goals of coalition data sharing and collaboration within the military and intelligence domains, is to empower and enable all allied partners and nations to communicate, collaborate and to be able to exchange and consume vital information in real-time – thus increasing and maintaining military effectiveness and dominance. From accurate weapon targeting, surveillance and intelligence gathering confidence, reduced redundancies and operational inefficiencies to preventing cross-coalition conflict - a unified command architecture is essential to efficiently utilize resources and increase effectiveness of operations. Coalition partners generally set standards for technologies and strategies to collect, share and parse data utilizing Command, Control, Computers, Intelligence, Surveillance and Reconnaissance architectures (C4ISR). For example, starting in 2019 the United States Army Mission Command selected Systematic's SitaWare (C4ISR) system that is designed to direct digital information for the warfighter across handheld, mounted, and command-post systems 5. For combined joint operations, complex environments made up of coalitions dispersed across the globe managing and exchanging highly classified and time sensitive data and thus require decisions to be made quickly and accurately. With so much information to be processed, it’s vital that operational headquarters personnel have the most advanced command and control tools available to them. These tools filter out noise and irrelevant information and facilitates improved coordination and collaboration across the mission theater 3.
Challenges across Coalitions
Complex coalition operating environments are continually exposed to logistical, security, social, and technological challenges. Harvesting, processing, and disseminating immeasurable volumes of data across the countless connected systems (in addition to storage challenges), vehicles, devices, assets, and personnel within the coalition is already riddled with problems before even considering integrating a shared architecture across a number of partner and allied nations. Therefore, it becomes highly important that requirements are clearly defined and understood by all partners within a coalition.
Coalition Unified Command
Coalition command is a costly and often an inefficient enterprise. Owl Cyber Defense states that unified command can slow data flows by forcing information to be redundantly processed at each tier of leadership. In order to leverage joint resources, requests must be sent and processed up the chain of command until the request arrives at the resource-controlling commander 3.
The cost of operating jointly manifests itself in the time and effort wasted dealing with bureaucracy and red tape which, leads to inefficiencies in information flow. However, the benefits of coalitions still outweigh the costs. But allied nations and coalitions need to address this problem to be at their most effective by streamlining unified military and operational activities.asd fasdf
Time Sensitivity
A unified command is only effective if data is processed in a timely manner. In military terms, the data sharing problem is also a problem of time, and the right information must be available to the right party.
The speed with which information can be generated, transmitted, collected, filtered, aggregated, synthesized, analyzed, processed, and turned around for orders or other dissemination is primarily determined by the amount of data generated, but also by the limitations of humans themselves 3.
Timeliness (or a lack of) is a key variable which, must be placed effectively as it can be the difference between actionable intelligence and missing a window of opportunity. This is very true during a military operation. It is imperative that any coalition C4ISR and collaboration solutions streamline this information lifecycle and reduce the time to action as much as possible.
Information Overload
The armed forces and military organizations are overwhelmed by data and information overload. The U.S. military, and by extension, its joint coalition force, is generating more data than it is able process. The coalescence of human intelligence (HUMINT), geospatial intelligence (GEOINT), signals intelligence (SIGINT), and open source intelligence (OSINT) in information generation and collection has created a mountain of information far too massive and steep. There is too much information to filter, sort and process for execution of actions and making effective decisions 3.
In addition, there are not only numerous data types, protocols, and media involved in the modern war theater, but multiple languages, security methods, and geographically and logistically disparate sources 3. This naturally lends itself to “Information Glut” and constricts the ability of command personnel from any coalition partner nation to utilize data effectively for timely action and during operations.
System Integration and Secure Collaboration
Large and complex coalition environments are usually diverse and have disparate technology and data touchpoints which, are globally dispersed. Such is the nature of complex environments. While the diversity of systems and data can be detrimental to performance and operational effectiveness. Coalition data sharing and collaboration solutions must harness the ability of data to overcome barriers and utilize common platforms and technologies to increase interoperability. Coalition systems must be able to securely communicate and collaborate with each other by the most efficient means possible.
Data and Infrastructure Security
As data will be shared across coalition partners traversing via the underlying infrastructure. It becomes highly apparently that there is a need for equal leveling across partners and the need for compliance and standardizing data, network and infrastructure security. Without this in place, coalitions expose themselves with a risk of having a “weak link” attack. An adversary or threat actor can exploit a network system with inferior security and gain access to information that would otherwise be protected if such standards were in place across all coalition partners.
Unless all partners in the coalition have equal protections for their sensitive information, including content filtering and confidentiality technologies and policies, they will be reticent to share any data at all. Any coalition data sharing solution will require cross domain content filtration capabilities as well as consistently enforced security policies 3.
Domain Separation
To supplement data and infrastructure security, there also remains a need to logically and/or physically separate domains. This ensures that data sharing will not enable lateral threat jumping, should a breach occur.
In the United States, information domains established by this separation must follow DoD policy and any partner nation restrictions, including any necessary risk assessments and determinations of authorized access. Coalition data sharing solutions will require domain separation at multiple points in the network architecture to segment and layer defenses 3.
Strategies and Solutions
There are a number of strategies and solutions, that if utilized and implemented properly, can overcome some of the challenges partner nations face within complex coalition environments. In this section we will review and illustrate a subset of potential strategies that coalitions may employ to be most effective within the mission theater. In addition, we will draw emphasis on MindLink’s own technology stack and product offering which, can be classed as a key technological contributor and differentiator within the coalition space. We’ll examine MindLink’s technologies and how these may alleviate some of the challenges we see today in complex coalition environments and how they may supplement other solutions that are being deployed and utilized across operationally effective coalitions.
To Design and Build Systems to Coalition Standards
To overcome the limitations of incompatible technologies, functionally equivalent but distinct software and hardware systems should be created and implemented across the coalition environment. In an ideal world, partners should collaborate to design and build such systems which meet a specific standard for security and fully support data integrity with the assurance that these systems meet the coalitions technology standards and compliance policies. The same rule applies, be it systems designed and implemented as in-house bespoke systems by a coalition partner or procured as commercial off the shelf solutions (COTS). Granted that some nations will build systems more suited to their local operational needs and there will be some differences in functional capabilities. But regardless, these systems must be designed, tested, operated, and sustained specifically with data interoperability as a key requirement, whether they’re built in-house or procured.
Consistency across coalition systems enables reliable data harvesting, sorting, filtering, storage and processing.
Big Data Artificial Intelligence (AI) and Machine Learning
Information overload and the processing of information at every level of command can create fatigue across the coalition organization. Time is categorized as a finite resource, and Artificial Intelligence (AI), Data Science (DS) and Machine Learning technologies are potential solutions to filter and process huge volumes of data and accelerate decision making and reduce the reliance on human intervention for data processing at various data process and exchange points across the coalition architecture and operational ecosystem.
AI and decision processing platforms normally require massive amounts of data which are processed through machine learning models.
AI takes advantage of vast data streams that currently sit untapped and lends itself to those tasks that occupy the most time, freeing people to think critically and creatively about how to win wars 3.
Domain Separation Solutions
Domain separation helps information security across a coalition networks. Owl Cyber Defense states that there is a pressing need for a “universal” cross domain solution (CDS) for use among coalition partners outside the Five Eyes (FVEY) 3.
Domain separation can be seen as a controlled interface – instilling a boundary with a set of mechanisms that enforces the security policies and access controls that adjudicate and monitor the flow of information between different disparate systems.
Cross-Domain Solutions (CDSs) are information domain separation systems that are capable of controlling and filtering data transfers between domains. The U.S. remains the technological forerunner that has already accredited solutions for immediate use within all partner nation networks – even those outside of the Five Eyes 3.
MindLink as a Solution
Any potential coalition data sharing solution must include strategies and technologies to reduce information waste and enable increased automation in information processing.
MindLink is designed to support mission critical use cases, like our coalition illustration above. MindLink is designed and well equipped to support real-time coordination and collaboration across globally dispersed military operations which are dependent upon high message volumes coupled with the mechanism to process intelligence.
The MindLink suite of products are diverse and extensible - at the center of its suite is the MindLink Chat Engine (MCE) which, supports a highly configurable, deployable and secure chat solution. Robust and scaled to support and facilitate global cross-coalition communication and collaboration.
We will put more emphasis on this section and refer back to some of the challenges that we discussed earlier and where the MindLink suite of products and solutions could facilitate and help solve specific challenges.
It could supplement and even facilitate communication and collaboration activities and integrate with an existing C4ISR system.
Information Overload and Time Sensitivity
As we learned above, coalitions require timely information to be processed by the right personnel. MindLink supports real-time message translation making it a truly universal collaboration tool. It can translate any incoming private or group messages to the target language. This is extremely valuable when coalition teams are coordinating operations with partners around the globe. Real time communication and collaboration are supported by the MindLink Anywhere web application. If personnel are out in the field, the MindLink Mobile application is fitted with an array of capabilities to keep communication lightweight and focused, ideal to support field operations.
MindLink gives coalition personnel an organized workspace which is completely customizable to suit a mission:
- Keep a precise and razor sharp focus on the task at hand. MindLink Anywhere’s whitespace management cuts out all of the noise and clutter that you will see in other chat applications.
- Folder management allows for better organization to group contacts and real-time chats that may be relevant to their specific part of the operation.
- Filters such as Hashtags, Mentions and Livestream help keep coalition partners and personnel engaged throughout all phases of a joint operation. As I mentioned earlier, every second counts and the strategy for success is speed and to stay ahead of the adversary – it must be “Real-Time”. Hashtags are useful to build topics which allow specialists to remain focused during a specific workflow. Mentions are useful to get immediate real-time attention of specific personnel handling a task or risk. The Livestream is a powerful feature that provides customizable real-time chat that appears within a widget focusing on specific chatrooms and contacts so personnel only see what matters to them most These filters help reduce the response time and speed up execution.
- Multiparty is a new feature that allows specific personnel to instant message and collaborate outside of a chatroom.
- 1:1 and Multiparty Voice call provides convenience of IP calling all within the same application. There is no need for another soft client to be installed – calls can be made through the MindLink Anywhere web application.
- Aliases and individual color coding of message easily help personnel see who is saying what within a chat stream.
System Integration and Collaboration
MindLink Anywhere supports applets and add-ins. Coalition partners do rely upon various tools to conduct their intelligence and operational activities. A majority of these tools facilitate information traversal across partners. In some circumstance It could possible to integrate these tools inside chatrooms if a webservice public API is available. For example, if a public API is available exposed by a C4ISR platform which gives engineers the capability to build custom applications and dashboards to present intelligence and operational data. This data could appear as an addin or applet inside a chatroom within MindLink Anywhere. The MindLink API could integrate with any C4ISR systems that has a support public API. This further widens the potential and possibilities to overcome barriers to achieving operation effectiveness, allowing coalitions to share data, communicate and collaborate more efficiently.
In addition, by using the MindLink API, it’s also very easy to build chatbots to relay, facilitate and govern collaboration within the MindLink ecosystem. Rules can be baked into the chatbot to trigger on certain operational events and signals.
IT Security and Compliance
MindLink’s infrastructure supports secure private-cloud and on-premise capabilities. The chat content stays within coalition partner’s or the wider coalition network perimeter. There is no risk of chat content being stored on a device or on an external cloud data array which could be prone to breaches or information leaks during transmission or storage.
Security is above key with Token based Active Directory Single Sign-on (SSO) baked into the web application. The MindLink Anywhere web application is stateless meaning that it maintains data privacy, where it does not hold message data in memory and encrypts data at REST and in transit using HTTP over TLS. Classification controls are built into MindLink Anywhere can further secure communication during an operation only allowing specific users to view specific messages based on classification markings.
MindLink features a unique enterprise end-to-end encryption capability which takes an innovative approach to zero-trust architecture using specialized information security paradigms adopted by the intelligence community. It leverages the "Communities of Interest" pattern to protect and exchange encryption keys whilst preserving both organizational governance and the scalibility required for effective mass-participation, real time collaboration. This mitigates prevalent insider threat against the vast attack surface of a typical chat system without compromising the capability of the system to support the modern mission.
The MindLink Mobile application is highly secure supporting End-to-End encryption and most of the major Mobile Application Management (MAM) solutions such as Airwatch, Mobileiron and Citrix Zen.
Classified Data and the Need to Know
MindLink Anywhere and MindLink Chat Engine leverage our built-in data classification capability which is the unique adaptation of military-grade labelling and access control techniques to chat rooms and messages using sophisticated national classification systems such as CAPCO as GSCP. It treats secure chat rooms as dynamically classified documents, performing message and room labelling, classification banner-rollup, and security clearance authorization. This secures classified data using government-mandated information management practices as first-class chat system constructs, whilst allowing the data to be shared frictionlessly in real time.
MindLink’s security architecture is rooted in the novel "Communities of Interest" paradigm advocated by the Intelligence Community. It segregates all aspects of the system - such as chat rooms, users, and content - into secure compartments to enforce strong access-control boundaries, define explicit data handling procedures, and mitigate spillage risks. This protects highly-sensitive information using best-practice techniques from the IC by ensuring data is organized and shared only with those with a "need to know".
Highly Deployable and Available
MindLink Anywhere supports all of the major browsers including Internet Explorer, Microsoft Edge, Google Chrome, Mozilla FireFox and Safari
MindLink integrates with cloud and on-premise chat solutions such as Microsoft Teams, Skype for Business Online, Skype for Business Online, Skype for Business 2015, 2019 (On-Premise) and its very own Chat Engine – MindLink Chat Engine (MCE) which is deployable to both on-premise or to a private cloud infrastructure.
MindLink is designed as a stand-alone solution for hosting in the private/public cloud and on-premise. It meets organizational requirements for uptime and scalability by deploying multiple nodes in a High Availability, Disaster Recovery or Load Balanced configuration.
References
1 Joint Vision 2010, Chairman of the Joint Chiefs of Staff, 5126 Joint Staff, Pentagon, Washington, D.C. 20318-5126
2https://www.rand.org/content/dam/rand/pubs/monograph_reports/MR1235/MR1235.chap2.pdf
3 Whitepaper - Overcoming the Challenges of Coalition Data Sharing by Owl Cyber Defense
4 https://media.defense.gov/2020/Oct/08/2002514180/-1/-1/0/DOD-DATA-STRATEGY.PDF
6 https://www.systematicinc.com/products/n/sitaware/headquarters-C4ISR-system/
Special acknowledgement to Owl Cyber Defense https://owlcyberdefense.com/